Technology & Manufacturing
Protect your IP and Easily Distribute Content
Prevent content from being copied, shared, or downloaded. Distribute content securely through a customized portal or business system.

Your digital content is at risk of being pirated, copied, or shared
As a digital content publisher or creator, your content can easily land in the hands of unauthorized users. It is at risk of:
- Being copied or shared
- Getting stolen or repurposed
- Being redistributed without your permission
Your teams spend a lot of time creating, marketing, and selling your content. By not securing it with DRM software, your resources are wasted. Don't let your work go to waste, protect your margins and bottom line!
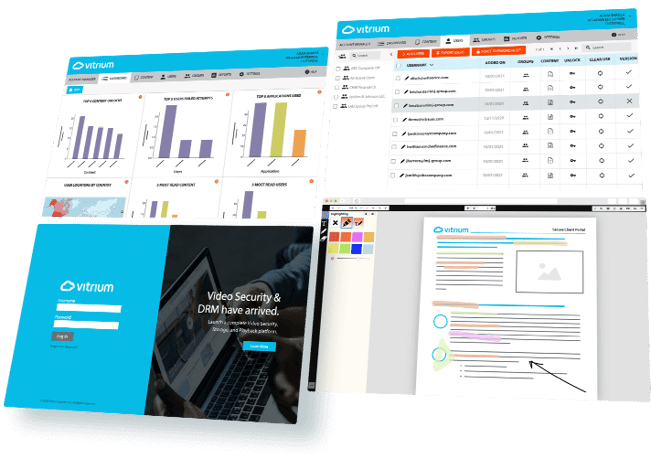
Vitrium protects your content and puts you in control
With Vitrium’s digital rights management (DRM) software, you regain control of your digital content.
You decide who has access and how they access it. You keep it exclusive to authorized users.
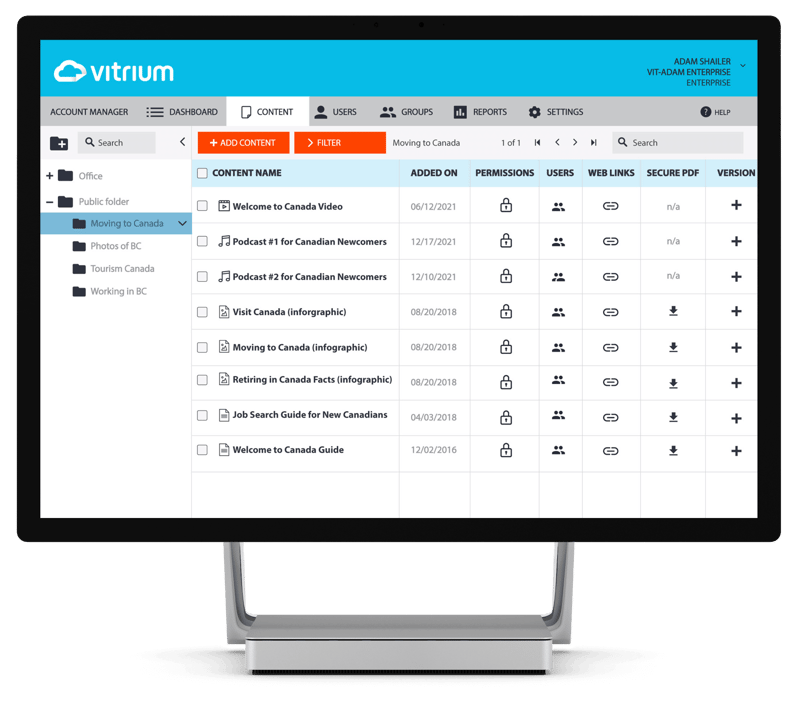
Advanced DRM Controls & Secure Distribution Methods
Content Protection
With all Vitrium solutions, your content will be protected with AES encryption and you can choose whether to allow or prevent printing, copying, downloading, or screen sharing.
Use Vitrium to protect your:
- Certification guides
- Design specs
- Training materials
- Price lists
- Audio content
- Images
- Videos
- And more
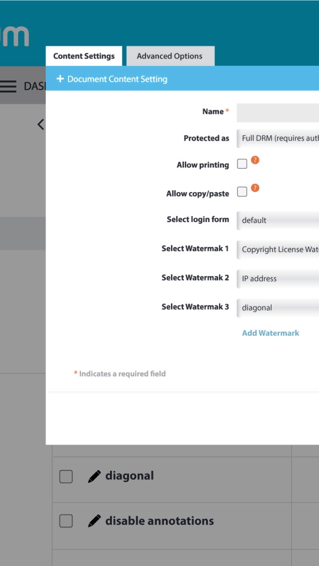
DRM Controls
Each Vitrium solution offers different digital rights management (DRM) controls for you to choose from. You can apply these to different users or groups, and for different content.
Apply a wide variety of different DRM controls:
- Prevent printing, copying or screen sharing
- Set expiry dates, device limits, or print limits
- Set open limits or account limits
- Apply user-identifying watermarks
- Control what IP addresses can access content
- Restrict or block certain countries
User Access
Depending on which Vitrium solution you choose, user access will vary. With all solutions you can leverage Vitrium’s advanced web viewer or Vitrium’s sleek on-demand video player.
With Vitrium DRM software, you can:
- Integrate with your LMS, eCommerce, or other business system
- Send an email to users with secure web links
- Enable single sign-on (SSO) to simplify user login experience
- Use Vitrium’s fully customized secure end user portal
- Add content into different folders or categories for easier access
Tracking & Analytics
Basic user tracking is available in VitriumOne and more extensive tracking is available in the two Vitrium Security products (Pro and Enterprise).
- Identify who is accessing your content, when, where and how*
- Look up user errors to help troubleshoot issues
- Drill down into analytical reports to gain insight into user behaviors
- Learn what your top performing content is
- Learn who your most active users are
- Set different date ranges for your reports
- Export your data for further analysis
*Current option available in VitriumOne. If you wish to see the other tracking features available in VitriumOne, contact our team today to discuss options.
Integration & Automation
Automate your workflows by integrating Vitrium DRM with your other business systems using Vitrium’s industry-standard REST APIs. Connect to 3rd party systems to provide single sign-on (SSO) access for your end users.
Depending on your Vitrium solution, you can integrate with:
- Learning management systems (LMS)
- Association management systems (AMS)
- Customer relationship management systems (CRM)
- Content management systems (CMS)
- eCommerce systems
- Member systems
- Databases
- Intranets or websites
- Other systems

Protect Multiple File Formats With Vitrium!
Vitrium’s DRM software allows you to protect documents, images, audio and videos. Vitrium encrypts these formats with 256-bit AES encryption and converts them to a secure web format.
Technology & Manufacturing Case Studies

ISA protects their exclusive content with Vitrium
ISA relies on Vitrium’s DRM software to protect their intellectual property and control distribution of global standards, technical reports, and recommended practices to professionals in the field of industrial automation.
IVES Training uses Vitrium to protect their IP
IVES Training, a provider of forklift certification training, initially used Vitrium since 2014 to protect their PDF-based Digital Training Aides but expanded their use of Vitrium in 2018 to protect their on-demand instructional videos.
“Integrating Vitrium Security Enterprise with our LMS has allowed us to protect our content and distribute it easily.”
Technology & Manufacturing Frequently Asked Questions
No, Vitrium does not use any proprietary or 3rd party plug-ins or apps.
Yes, all Vitrium solutions can protect video content, as well as documents, images, and audio files. All content is converted to a secure web format, so videos can be streamed at different resolutions.
Yes, all Vitrium-protected content is delivered through a secure web format that can be accessed on any device using any browser.
Yes, this is possible for documents, images or audio, and you can control this setting in your DRM Policy in Vitrium. However, offline access is currently not available for video content, because the content is delivered via a web format and relies on the browser’s memory which is limited.
Yes, Vitrium Security Enterprise uses rest APIs to integrate with multiple business systems such as: eCommerce systems, Customer Relationship Management systems (CRM), Content Management Systems (CMS), Member systems, Websites, and many more.
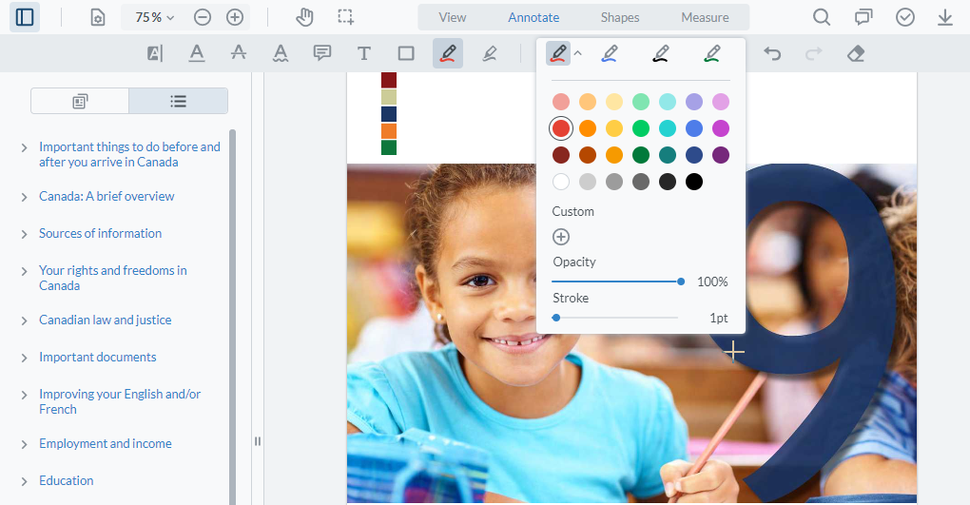
Yes, these features are available in all Vitrium products. Students access their secure content via the Vitrium Viewer, a sleek, modern web viewer that comes with extensive annotation controls and numerous color and styling options.
See Vitrium in Action
CONTACT US
© Copyright 2026 Vitrium Systems Inc.