Associations & Standard Development Organizations must keep their content protected. DRM software is the solution.
How Does DRM Work? A Comprehensive Guide to DRM Protection
In today's digital landscape, protecting sensitive digital content such as documents, PDFs, eBooks, and videos, has become a critical concern for organizations. To address this issue, Digital Rights Management (DRM) software offers a highly effective solution for safeguarding valuable content from unauthorized access and distribution.
This article aims to provide a comprehensive guide on how DRM works, its role in content protection, and the significance of using DRM software for enhanced security as well as the well-being of an organization.
1. Understanding DRM & Document Protection:
1.1 What is DRM?
DRM, or Digital Rights Management, is the technology used to control access, usage, and distribution of digital content. It is a set of policies, permissions, and restrictions that confer content providers and distributors complete control over their content. DRM enables content creators and distributors to protect their intellectual property and ensure that only authorized users can access and utilize the content.
1.2 Why is Content Protection Important?
Documents, PDFs, and eBooks often contain sensitive information, proprietary knowledge, or copyrighted material. Unauthorized access, copying, or distribution of such content can lead to financial loss, privacy breaches, and copyright infringement. Document protection through DRM helps prevent unauthorized access, restricts content usage, and minimizes the risk of intellectual property theft.
2. How DRM Protection Works:
2.1 Encryption: The Foundation of DRM
Encryption forms the foundation of DRM technology. Robust algorithms are employed to encrypt the content, rendering it indecipherable without the appropriate decryption key. By implementing encryption, DRM effectively prevents unauthorized individuals from gaining access to the contents of the file.
2.2 Licensing & Authorization
DRM utilizes licensing and authorization mechanisms to regulate access to protected content. Users are required to obtain a license or permission from the content owner or distributor in order to access the protected files. This authorization can be granted through different methods, including license keys, digital certificates, or online authentication.
2.3 Access Control & Permissions
DRM allows content creators to define and enforce access control policies for their documents. These policies determine who can access the content, under what conditions, and with what permissions. Access control mechanisms may include password protection, user authentication, time-limited access, or restricted viewing/printing options.
2.4 Watermarking & Traceability
DRM systems often incorporate watermarking techniques to discourage unauthorized distribution. Watermarks can be visible or invisible and may contain information such as the user's identity or transaction details. If unauthorized copying or sharing occurs, watermarks help identify the source of the leak and deter further misuse.
Understanding DRM Protection for eBook Security:
DRM software adds multiple layers of protection to eBooks, keeping them secured and exclusive to authorized users. A quality DRM solution will include the following:
- Encryption: DRM technology encrypts eBook files, making them unreadable without proper decryption keys. This prevents unauthorized access and ensures that only authorized users can decrypt and read the content.
- Access Controls: DRM enables content providers to control who can access their eBooks. By implementing access controls such as username and password requirements, publishers can restrict access to authorized users only.
- Usage Limitations: DRM allows publishers to define usage restrictions, such as limiting the number of devices on which an eBook can be accessed, the number of times it can be viewed, the amount of time content is available for, whether or not it can be downloaded or printed. This gives the content provider complete control over their eBooks, and allows them to determine how their content will be accessed and consumed. Having control of digital content helps keep it secure.
- Watermarking and Tracking: A quality, high security DRM system will include watermarking capabilities to embed unique identifiers into eBooks. These user-identifying watermarks deter users from incurring in copyright infringement. If unauthorized copies of the content are found, the watermark can trace them back to the original purchaser, discouraging piracy.
Benefits of DRM for eBook Security:
Implementing DRM for eBook security offers several key advantages:
- Protection against Piracy: DRM significantly reduces the risk of unauthorized copying and distribution, discouraging piracy and safeguarding the revenue of digital content creators & distributors.
- Secure Distribution Channels: DRM enables secure distribution through authorized channels, ensuring that only legitimate users can access the content.
- Flexible Usage Control: DRM allows providers to define usage rules, including the ability to lend eBooks or provide temporary access, striking a balance between convenience for readers and content protection. Additionally, a quality DRM software will allow content providers to provide an excellent user experience to their audience.
- Increased Revenue Potential: By protecting eBooks from piracy, DRM helps maximize revenue potential for authors and publishers, allowing them to produce more quality content.
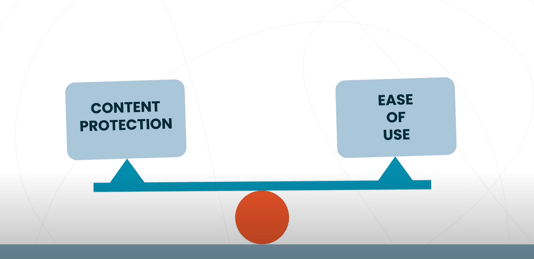
Balancing eBook Security and End User Experience:
While eBook security is crucial, it is equally important to maintain a positive user experience. Striking the right balance ensures that readers can access and enjoy their eBooks seamlessly while protecting the rights of content creators. Publishers should consider user-friendly DRM solutions, like Vitrium, that provide adequate security without overly restricting legitimate users.
Vitrium offers numerous features that make the end-user experience pleasant. From single sign-on capabilities, to a modern web viewer with multiple annotation tools and collaboration features, Vitrium customers can make sure they’re offering the very best experience to their audience.
Conclusion:
As eBooks continue to gain popularity, it is essential to prioritize eBook security and the implementation of DRM in order to protect the rights of authors and publishers. By leveraging DRM technology, content creators can effectively safeguard their intellectual property, deter piracy, and maintain control over the distribution and usage of their eBooks. Embracing DRM not only ensures a secure reading experience but also contributes to the long-term sustainability of the eBook industry.
Remember, prioritizing eBook security through DRM is an investment in protecting intellectual property, fostering innovation, and supporting the future of digital publishing.
Vitrium and eBook Security:
Vitrium software thoroughly protects your eBooks, ensuring your IP is not copied, downloaded, or shared with unauthorized users. You remain in complete control:
- Protect your eBooks & convert them to a secure web format & a downloadable protected PDF
- Prevent printing, downloading, copying or sharing
- Apply and customize user identifying watermarks
- Set expiry dates, device limits, open limits & control access by IP address or location
- Provide your users with online and offline access
- Access content in a browser, a user portal, or your website
- Integrate with 3rd party systems
- Provide single sign-on (SSO) access
- Identify who is accessing your PDFs, when, where, & how
Ebook security is crucial for the well-being of your organization. To guarantee content is kept private and protected, to prevent tampering with your intellectual property, and, ultimately, to secure your revenue streams and bottom line.
If you'd like to learn more about protecting PDFs and other types of digital content with Vitrium, please don't hesitate to get in touch with us, we'll be happy to answer any questions you have.






