The ultimate guide to a robust digital rights management (DRM) solution
Introduction
There are numerous different features that one should look out for in a content protection and digital rights management (DRM) software solution. This article outlines the significant ones which fall into one of the following categories:
Learn the best way to protect your IP
Content Protection & Encryption
Any content that can be easily copied, printed, or shared isat risk of piracy, intellectual property (IP) infringement, mass redistribution, leaks, plagiarism, data breaches, and so on.
Particularly vulnerable is content that generates revenue for a business or contains confidential information, trade secrets, financial information, or content that is otherwise sensitive in nature. So in this digital age, what are firms to do?
The first line of defense that comes to mind is to add password-protection on a file. Although passwords can restrict file access, they are often easy to share, easy to crack, and difficult to manage for more than a single user.
Watermarks are also considered and they’re an excellent feature to deter copyright infringement, but not restrictive enough on their own. Adding a dynamic watermark that includes user identifying information such as a user name, user ID, company name, etc. definitely takes things a step further, but again, not restrictive enough on its own.

The best measures are to add strong, military-grade encryption. With this option, you’re essentially converting your unprotected content to a non-readable, encrypted format that can then only be unencrypted when you receive the encryption keys or you’ve been authenticated against another system. The most common encryption level offered by many file sharing and virtual data room providers is disk-level encryption. At this level, only the directory containing the files is encrypted while individual files remain unprotected and still vulnerable to leaks, unauthorized sharing, piracy and other potential hacks.
A great analogy for disk-level encryption is protecting your house with a lock and security system, but leaving all your valuables inside unprotected. A robber could bypass the lock and security system, and then gain access to whatever they find in the house. However, by applying file-level encryption and control in addition to the disk-level encryption is analogous to having a robust digital rights management (DRM) system like Vitrium which protects both the house (or portal / data room where the content resides) and the valuables within the house (the files within the portal or data room). By applying file-level encryption and DRM controls, this secures all the individual files and enforces protection no matter where the content resides.
Ready to see if password protection will reduce the loss of your content?
Vitrium offers password-protection, hidden and dynamic watermarks, and file level encryption.
User Access Control with DRM
User access control is not a zero or one concept anymore. Digital rights management (DRM) technology allows content owners to determine how different audiences could access different files.
Granular DRM policies have empowered many content producers and publishers to offer multi-tiered subscriptions and membership plans to meet different segments’ needs, increase their revenues, and stay competitive. That’s great for revenue-generating content but how does it help for confidential or sensitive files that don’t generate revenue for a business but are still equally important to protect?
Due to their sensitive nature, confidential files may also require different types of user access controls. For example, you may want to provide different levels of access control for companies that are in different stages of a merger & acquisition (M&A) deal. Maybe for those companies that are in the early stages of a deal, you decide to only provide them 1-week access to content and you set a 1-device limit for each file in your data room, but then for companies that are in the later stages (say the due diligence phase), then you provide 30-day access and a 5-device limit for each file knowing that content needs to be shared among more people within the company.
When it comes to user access control, the first and most critical function is the ability to grant and revoke access anytime, no matter where a file resides or who it is shared with. Once you are assured that your content is within your control all the time, another valuable function is the ability to set up more granular restrictions.
A comprehensive digital rights management (DRM) system like Vitrium encompasses numerous different user access controls including:
- Expiration limits - a specific date or number of days when content should expire
- Start date - a date when a user can first access the content (ideal for subscriptions, the start of a school term, or the start of an RFP process)
- Device / browser limits - how many devices (or browsers) a user can open content on
- Print limits - how many times a user can print content
- Open limits - how many times a user can open or view content
- IP address limits - how many IP addresses a user can open content from
- Specified IP address - which IP address (or range of IPs) a user can open content from
- Country or state limits - which country(ies) and/or state(s) a user can open content from or, the opposite, which country(ies) and/or state(s) users cannot access content from
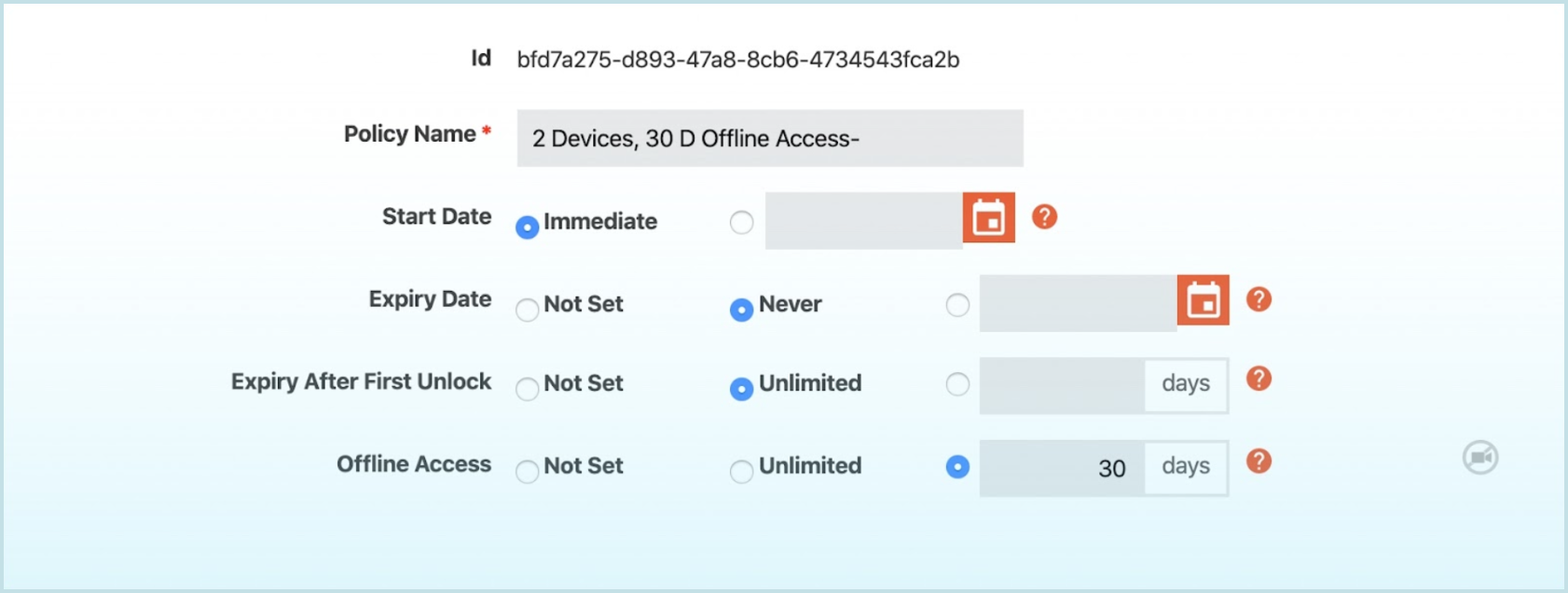
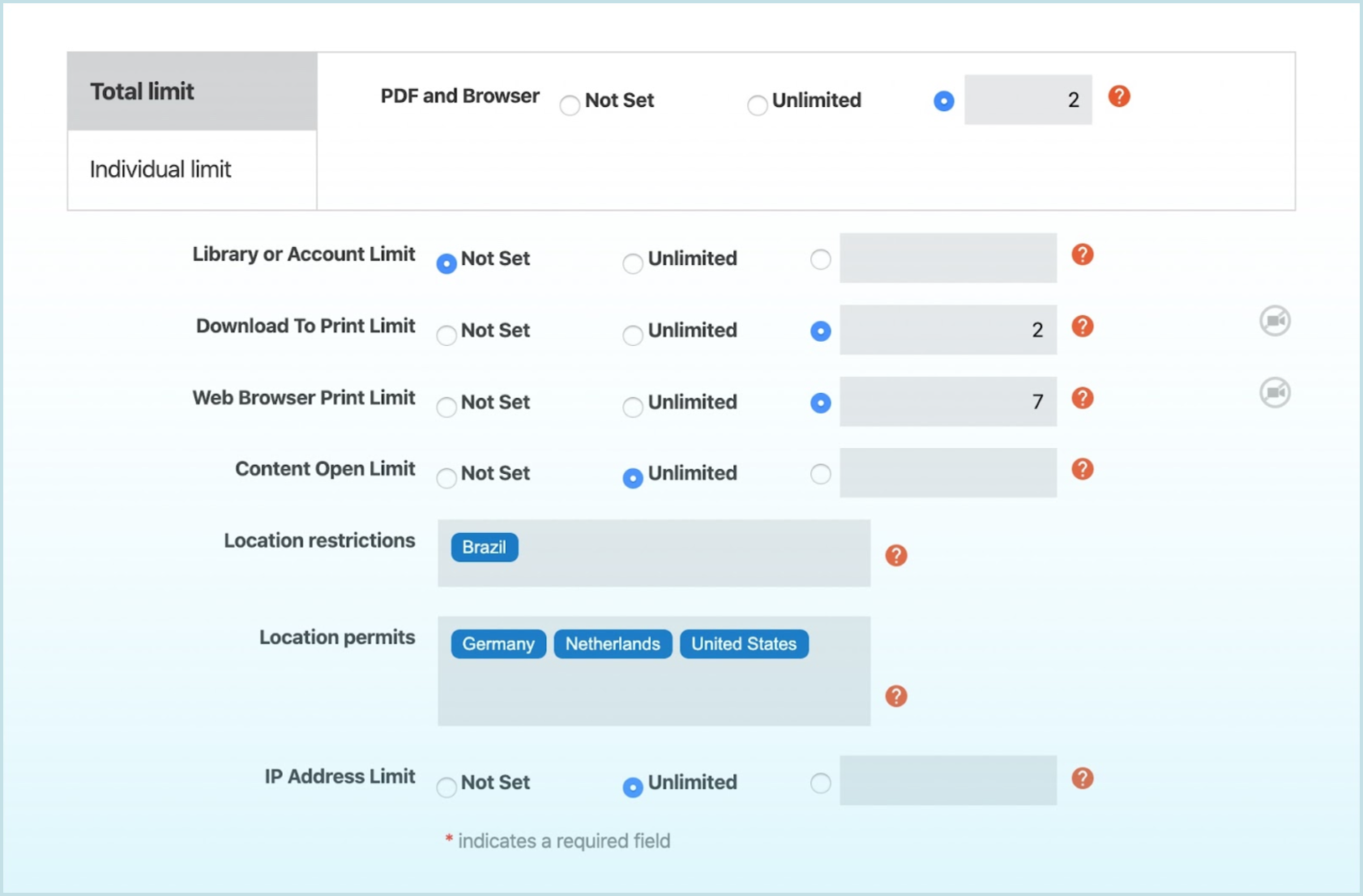
Leveraging flexible DRM controls, you can define different access control policies for different audiences or stakeholders. For example, you may only want your certified partners to access certain confidential or IP-related materials such as new price sheets and technical guides associated with a new product line you’re about to release. You can provide access to those certified partners based on their IP addresses and perhaps also limit them to opening the content on a certain number of devices. Alternatively, if you have a select few other contacts that you would like to provide access but they have not been designated a ‘certified partner’ yet, you can assign them permission to the content but apply a more restrictive policy such as access on 1 device only, no printing, and no copying based on their non-partnership status.
This flexibility can be extremely valuable for companies that operate with a subscription-based model. Let’s take the example of a research firm that distributes a highly-sought price reports for the commodities sector.
They offer 3 different subscription plans to their clients, all with different price points and different offerings: (1) Bronze, (2) Silver and (3) Gold.
Here is an example of how tiered subscription plans like this can take advantage of flexible DRM access controls.
In the “Gold” plan
users pay a hefty premium fee but they receive unfettered access to the commodities reports with unlimited device use, unlimited printing capabilities and access across the globe.
In the “Silver” plan
users pay a premium fee but not as hefty as the Gold plan and they receive access to the reports on 10 devices, 5 prints and access in 5 countries of their choice.
In the “Bronze” plan
users pay a standard fee and they receive access to the reports on 2 devices, 1 print and access only in 1 country of their choice.
The more comprehensive and flexible your DRM access controls are, the more diverse permission levels you can set, and the more revenue you could earn by up-selling to the more lucrative subscription plans.
Ready to see if password protection will reduce the loss of your content?
Vitrium offers time limit access, browser and IP limits, nation state restrictions, and more.
Secure File Sharing & Content Distribution
Undoubtedly, a solid content protection and DRM software like Vitrium makes file sharing a secure and straightforward process. A secure digital file sharing and content distribution system like Vitrium diminishes printing and shipping costs while streamlining the delivery of content.
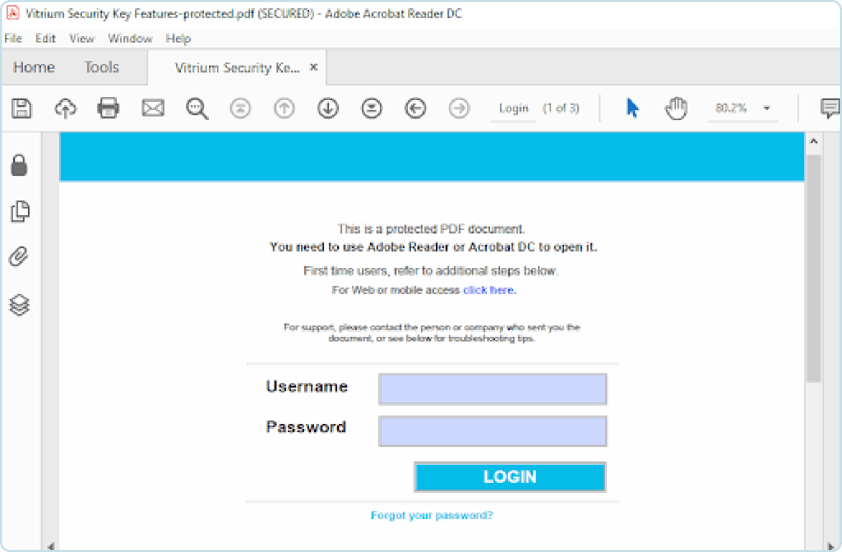
Vitrium converts files into two encrypted formats: A secure web viewer that can be viewed or accessible in a web browser on any device A protected PDF file that can be downloaded and viewed with Adobe Reader The Bonus: neither format requires the end user (recipient) to download any plug-ins or third-party apps to view the content.
Secure File Sharing & Content Distribution
With Vitrium’s secure web viewer, it’s a simple, yet very secure URL that can be easily shared from one person (or company) to another. It can be included in an email, posted on a website, or embedded in a system like a learning management system (LMS), association management system (AMS), eCommerce system, or other system where content is distributed to users. Vitrium’s secure web viewer not only makes file distribution simple but also eliminates the hassles and costs of file storage.

Protected PDF File
Despite the rising demand for and the wonderful benefits of the secure web format, there are still people who prefer the traditional PDF format, maybe because it’s what they’ve always known or they simply like the idea that they can ‘see’ the file within their possession on their local hard drive or company network. To serve this type of audience, Vitrium also converts documents into a protected PDF format. The benefit is that the security remains with the protected PDF files no matter where they’re downloaded or saved. These secure files can also be distributed by email (if they’re small enough), or added to a website, or third-party system mentioned above (LMS, AMS, eCommerce, etc.) and downloaded by authorized users to their local machine or favorite cloud account. Since the security travels with the protected PDF files, you can be assured that you still maintain full control of your content no matter where this file resides. “How”, you ask? Well that’s our secret sauce! But we can let you in on some of the secrets if you call us.
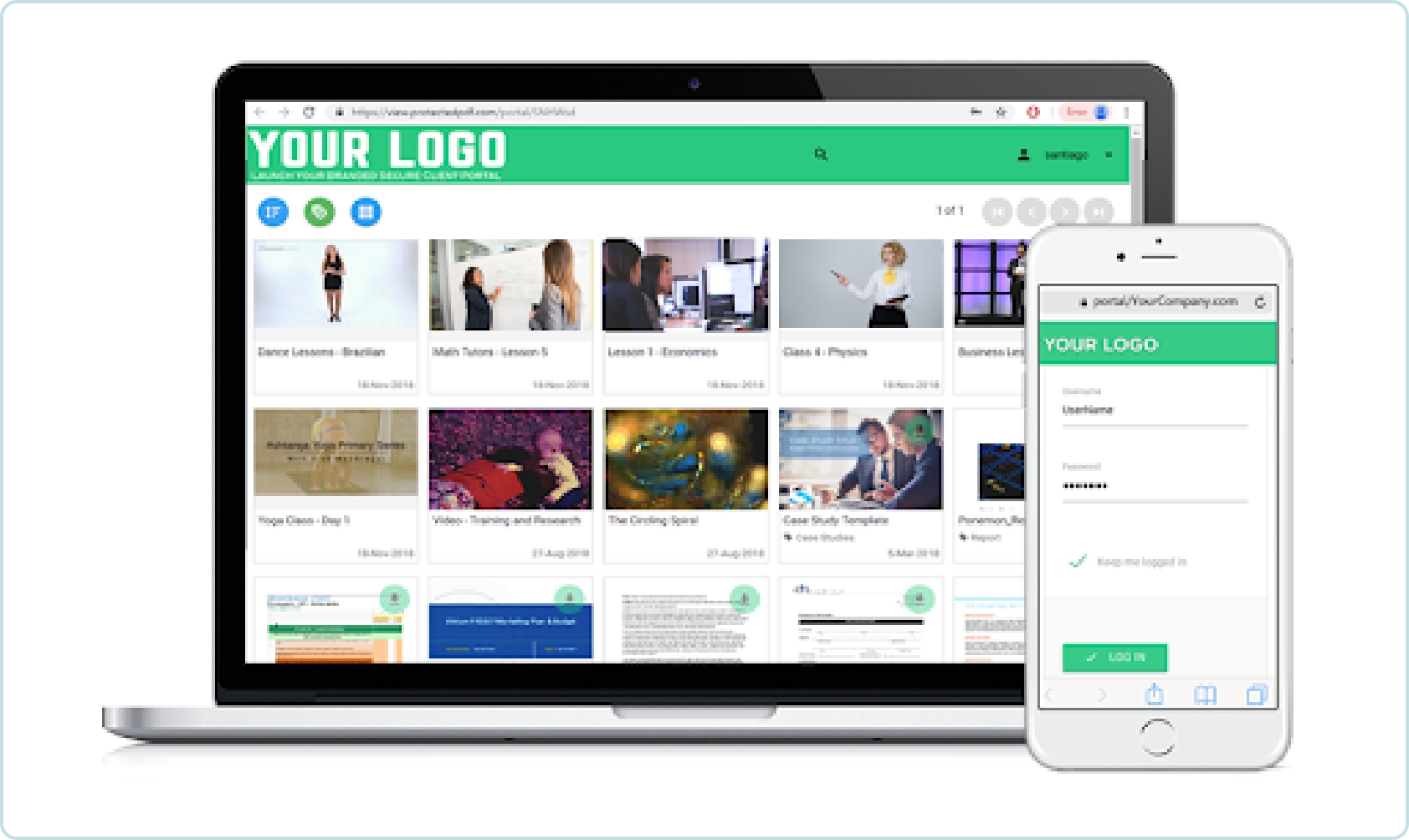
Virtual Data Room / Secure Portal
If you’d like to offer your clients a central, secure place where users can access multiple files in once place, you can take advantage of Vitrium’s virtual data room (VDR) or secure portal as some may call it. You can even make it your own by adding your logo, brand colors and even use your own domain URL. Many VDR and data room providers in the market make you set up different data rooms which can be a hassle, especially if many of them require the same content to be shared. With Vitrium, you only need to create data room or portal. On the administrative side, you can add your content into different folders for different clients and assign permissions to specific users (or clients) at each folder level so the user only sees the content for which they’ve been assigned permissions to view.
Leverage SSO With Your Website or System
Vitrium’s Enterprise Edition integrates with virtually any website or third-party system like eCommerce systems, learning management systems (LMS), content management systems (CMS), association management systems (AMS), CRM systems, and more. By integrating Vitrium with your existing business systems, offering users single sign-on (SSO) functionality, and tying the content distribution (secure file sharing) methods with your existing workflows, this can go a long way to streamline your entire workflow process, especially for the end users who may be your clients, subscribers, members, students, partners, or others.
Every piece of content deserves to be protected.
Vitrium offers time PDF protection, video protection, virtual room, and content distributed via your website.
User & Content Tracking & Analytics
An indispensable element of good content protection and digital rights management (DRM) solutions is its tracking and analytics capabilities. After you’ve protected your content, assigned the right DRM access controls and distributed your content, you’ll want to track the usage and monitor how your content is being consumed.
Vitrium provides you with some of the most extensive user activity reports and detailed drill-down analytics in the market among DRM or virtual data room providers.
![]()
The most important report is the User Activity Log where you can track who has accessed your content, which files, on what date and time, from which IP address, browser or application, and even their operating system (OS). This level of user activity tracking not only provides you with insightful data about who your most active users are or which content is most popular but it also allows you to spot any suspicious activity. For example, if you notice that a user has tried to access your content from several different countries or IP addresses in a short amount of time, this could be a sign of unauthorized sharing or distribution, or worse, content piracy. Of course, you can eliminate this from occurring by setting more restrictive DRM access controls such as applying device limits, IP address limits and setting country restrictions (i.e. only allowing access in the USA for example).
With Vitrium’s detailed analytics reports, it opens your eyes about how your users are engaging with your content. You can find out which content has the highest read-through-rate (for documents), view rate (for videos), or which users are the most actively engaged with your content.
Vitrium’s analytics can provide you valuable insight for your business and drive you to make strategic decisions to lead to more prosperity for your business.
Ready to see what tracking and analytics features are the right fit for your business?
Vitrium offers content tracking, user activity logs, drill down analytics reports, and more.
Smooth & Seamless End-User Experience
A quality DRM solution will not hamper your end users' experience. It will provide the ideal balance between content protection and ease of use.
DRM solutions of the past have indeed posed challenges especially if they required the user to download some form of plug-in, app or third-party proprietary software to view or decrypt content. And some of those providers are still around today!
Vitrium’s offering is not that as the company’s focus for the past 15 years has been finding the right balance between the needs of content publishers/owners/distributors to protect their confidential content or intellectual property with the needs of users who just want to access their content immediately, seamlessly.
A sophisticated content protection and DRM software like Vitrium prevents unauthorized users from accessing content while providing the authorized users (the right audience) with a smooth and seamless experience.
If you decide to use Vitrium ‘out-of-the-box’ with no third-party integration, all the end user needs to do is enter their login credentials. These can be supplied by you or you can force the user to create their own when they first access content. If you use Vitrium’s Enterprise Edition and you have the software integrated with your website or third-party system with single sign-on (SSO) set up, then the user just accesses their content through their usual methods (maybe via an email with a link to the content, or via their My Orders or My Content page of your website) and the content will immediately ‘authenticate’ the user and the permissions are passed through API calls. The users themselves don’t often realize there’s protection or DRM controls put on the content they’re accessing…..it’s that seamless! However, if they try to share the content with someone who isn’t authorized, that person will be denied access, providing you the level of protection and control that you need. All of this is tracked in your Vitrium User Activity Log as well.
Don’t disrupt your audience, whether it’s your clients, partners, subscribers, members, or students with clunky and messy plug-ins or 3rd party apps. Downloading, installing, updating and other compatibility issues exhausts people and they will lose interest in your content. Vitrium’s “no plug-ins or apps” approach lets you and your users enjoy a seamless experience.
Moreover, Vitrium’s secure web viewer allows end users to access your content on any device via the Internet with all the highlighting, note-taking and other annotation tools they may need. End users don’t need to worry about saving files or using up storage on their hard drives or cloud accounts. And they can even access the content while offline with Vitrium’s unique ‘save-to-browser’ feature!
For those more traditional folks who just need to ‘see a file’.....you can send them the protected PDF and they can download this file to their local machine, company network or cloud account. The document is protected at all times giving you peace of mind but it can be viewed by the authorized user with the popular Adobe Reader application.
Don’t hinder your content with protection. Just keep it from piracy.
Vitrium offers content protection without apps or plugins required.
Integration With Other Systems
It is crucial for a content protection and digital rights management (DRM) solution to be able to easily integrate with a wide variety of third-party business systems.
Many types of companies across different industries create, publish, and distribute content that needs to be protected. And therefore, the DRM system needs to be able to integrate with a variety of different systems including:
- Learning management systems (LMS)
- Content management systems (CMS)
- Association management systems (AMS)
- Customer relationship management (CRM) systems
- eCommerce systems
- And more!
With industry-standard REST APIs, Vitrium’s Enterprise Edition software has been integrated with numerous off-the-shelf, custom and proprietary systems falling into one of the categories above. Integrations are ideal if you wish to automate any of your content workflow processes - the contention protection process, the user administration process, but the number one reason is to enable single sign-on (SSO) functionality in order to make the content access for your end users as seamless as possible. After all, if you already manage users (let’s say students) in a learning management system (LMS) and you have your content within that system, why would you want students to enter a separate login to access said content? It’s much better if the content has been protected with Vitrium and the user simply clicks on the content with the LMS and is automatically authenticated and authorization permissions are passed to the user…..all within milliseconds, without the user even realizing what just took place!
Intimidated by protecting your content?
Vitrium offers single sign on, LMS, CRM, integrations that make sharing your content as easy as saving it to your drive.

Curious which DRM solution is best for your business?
CONTACT US
© Copyright 2026 Vitrium Systems Inc.