DRM is the software that allows organizations to protect their digital content, such as documents, images, PDFs, videos, & audios.
Hassle-Free Protection: DRM can be a Simple Solution
Understanding the importance of intellectual property protection and settling on the idea that securing your intellectual property (IP) must be a top-priority for your company. Protecting documents, PDFs, eBooks, images, videos, audios, etc. with DRM software is crucial. This brings the need to develop a protection strategy that is holistic and, at the same time, enables ease of use.
Understandably, this process can be overwhelming and confusing, as there are many misconceptions around what digital rights management (DRM) actually is, how it differs from encryption, how it works and how it is executed. However, implementing a DRM strategy does not need to be cumbersome and stressful for you or your end-user. Moreover, content protection is extremely important for the well-being of your company, and therefore should not be overlooked.

Digital rights management very broadly refers to the software programs that are created for the purpose of helping companies protect their valuable content and intellectual property. As Tech Target has correctly explained, a digital rights management strategy supposes a “systematic approach” to the protection of “digital media.” Online piracy is a very real, very serious threat, and DRM has come out of the need to “prevent unauthorized distribution of digital media and restrict the ways consumers can copy content they’ve purchased.”
Digital rights management steps in where “hit-and-miss strategies,” that are focused on “apprehending online poachers” after they have stolen, copied, or unlawfully distributed valuable content, lack. It is the technology that allows content providers and creators to make stealing impossible in the first place, rather than finding and punishing those who have.
How DRM Differs from Encryption
Part of what makes digital rights management confusing or complicated is the fact that it is often mistakenly used in parallel with encryption, that is, it is often assumed that DRM and encryption are the same thing. While they are both a part of the same solution, it is not correct to use them interchangeably.
DRM is a complete strategy that incorporates and makes use of many different elements, one of which is encryption. Thus, encryption is a part of the content protection plan, rather than the digital rights management plan itself. File encryption is “the first step” to a robust “DRM deployment, but it’s not the only step” as Christopher Levy, CEO & Founder of Buy DRM, has explained. It usually takes place when uploading files to a secure portal and, additionally, it allows for files to remain protected wherever they go.
The idea behind encryption is to initially prevent tampering or modifying of the content. Then, further digital rights management settings are set to ensure content is protected through and through.
How Does DRM Work and How is it Implemented?
Digital rights management (DRM) works by implementing different sets of policies that allow for the prevention of piracy and the protection of valuable intellectual property. These policies, or control techniques, are applied at different levels and are dependent on the degree of security that is needed according to the sensitivity of the content to be protected. Naturally, highly sensitive content will require stricter, more restrictive policies.
Essentially, as put by Gabe Russel from Brightcove, “content is stored and transmitted in an encrypted form,” so that it can be accessed exclusively by authorized users.
When attempting to access the protected file, the user will be required to provide authentication details which will then
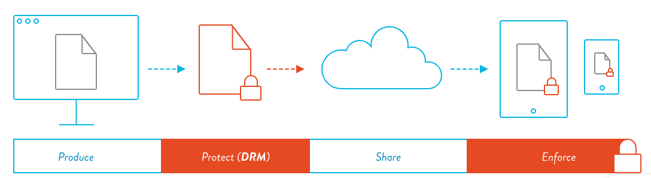
issue a response of approval or denial. Then, additional policies will be added. The content provider can choose to protect their files at different levels and add more or less restrictive policies depending on the type of content. The encryption of files and further application of these content controls, which include print and copy restriction, static or dynamic watermarks, device limits, location restrictions, and IP address limits, will effectively result in the successful implementation of a DRM strategy and, naturally, in the protection of valuable content.
Moreover, when your system is fully integrated with the DRM software you choose to use and you offer single sign-on, your users will most likely be unaware that your content is being protected, making their experience simpler and more enjoyable.
What Does DRM Look Like for End-Users
Depending on the DRM strategy you choose, your user experience will be different. However, users will generally always have to provide credentials that authenticates them as authorized individuals.
If the system you are using is not integrated, your DRM solution will work like a secure portal in which each secure file will be safely stored. Authorized users will go into this portal, which can be fully customizable to your brand identity, and access the files they have been licensed. It’s a simple, straightforward process, by which you provide content for your users all in one place, while ensuring that it is protected and will not be copied or re-distributed.
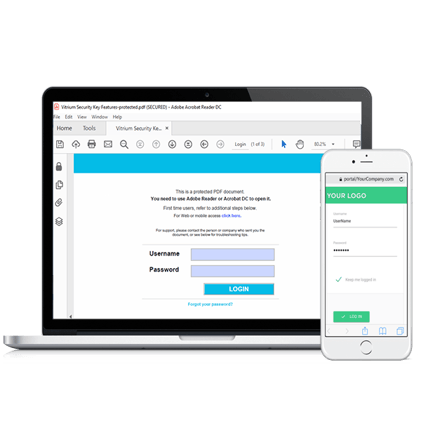
Conversely, if you choose to fully integrate your DRM solution with your system, you will then be able to grant single sign-on to your users. Your secure content will be accessed through your website, which means that your users will not need to open additional links or login elsewhere in order to access the content they have paid for. It’s comfortable and easy for them, yet extremely secure for you. In both of these instances, policies and restrictions can be set up at various levels depending on how strict you want your security to be.
By setting policies that have diverse degrees of restriction or leniency, you can sell your content at different price-points. For example, you can limit access to a single device for your most basic subscription, and progressively include more devices and/or the possibility to clear device history for those at a higher price-point. In this regard, DRM not only allows you to protect your revenue by protecting your content, but it also will give you the opportunity to market and sell your content and increase your revenue.
Moreover, there are quality DRM solutions, such as Vitrium, that make this process even simpler. By being available as cloud-based solutions or standalone products with a secure portal for users to log into, or by being fully integrated with the programs or systems already being used (such as learning management systems, content management systems, or association management systems), novel DRM solutions may work for you in a way that your users may never even realize your content is protected with DRM controls.
By signing up with Vitrium Security, a simple, hassle-free DRM solution, your content can be protected in as little as one day.
Learn more about our software, click here to request a free demo!