It’s never been more critical to protect digital assets. Learn how to have a secure data room that also protects the digital assets within it.
The Power of Advanced DRM Controls for Secure Data Rooms
Every digital asset your company owns - documents, videos, images, and audio files - they are each valuable in their own way. While some pieces may be more valuable than others, together they create a body of intellectual property that, under the hands of unauthorized users, can quickly transform into a body of liabilities. A company’s best line of defense to prevent unauthorized access is combining a secure data room with a digital rights management (DRM) solution.
Though some security breaches may be innocent, such as sharing files on social media with no ill-intent, most breaches are malicious with financial gain being the goal. Since 2005 there has been a significant increase in data breaches year over year according to Statista with roughly 157 data breaches in 2005 and 1,473 in 2019 respectively in the United States alone. The breaches that occurred in 2019 resulted in “over 164.68 million sensitive records exposed.”
According to a May 2020 report from CSO Online, "The average cost of a data breach has risen to $3.92 million,” which can be devastating to a company’s bottom line and could even result in them closing their doors entirely. They also stated that "The size of the average data breach is now 25,575 records, an increase of 3.9% compared to 2018." What could a breach of that size do to your organization?
CSO Online acknowledged that beyond the initial costs organizations face in the event of a data breach, they also suffer damage to reputation, a decrease in stock value, and an increase in customer turnover. However, with the proper content protection and DRM measures in place, the risk of data breaches is significantly reduced.
How Can Advanced DRM Controls in a Secure Data Room Aid in Preventing Data Breaches?
You may have the best network security measures in place but what happens when important files or content are shared externally with your clients, partners, or contractors? Having a secure data room can help.
Better yet, combining a secure data room with a digital rights management (DRM) solution provides your intellectual property (IP) with complete digital asset protection. Not only is each piece of IP locked away in a secure data room, but it also adds file-level protection.
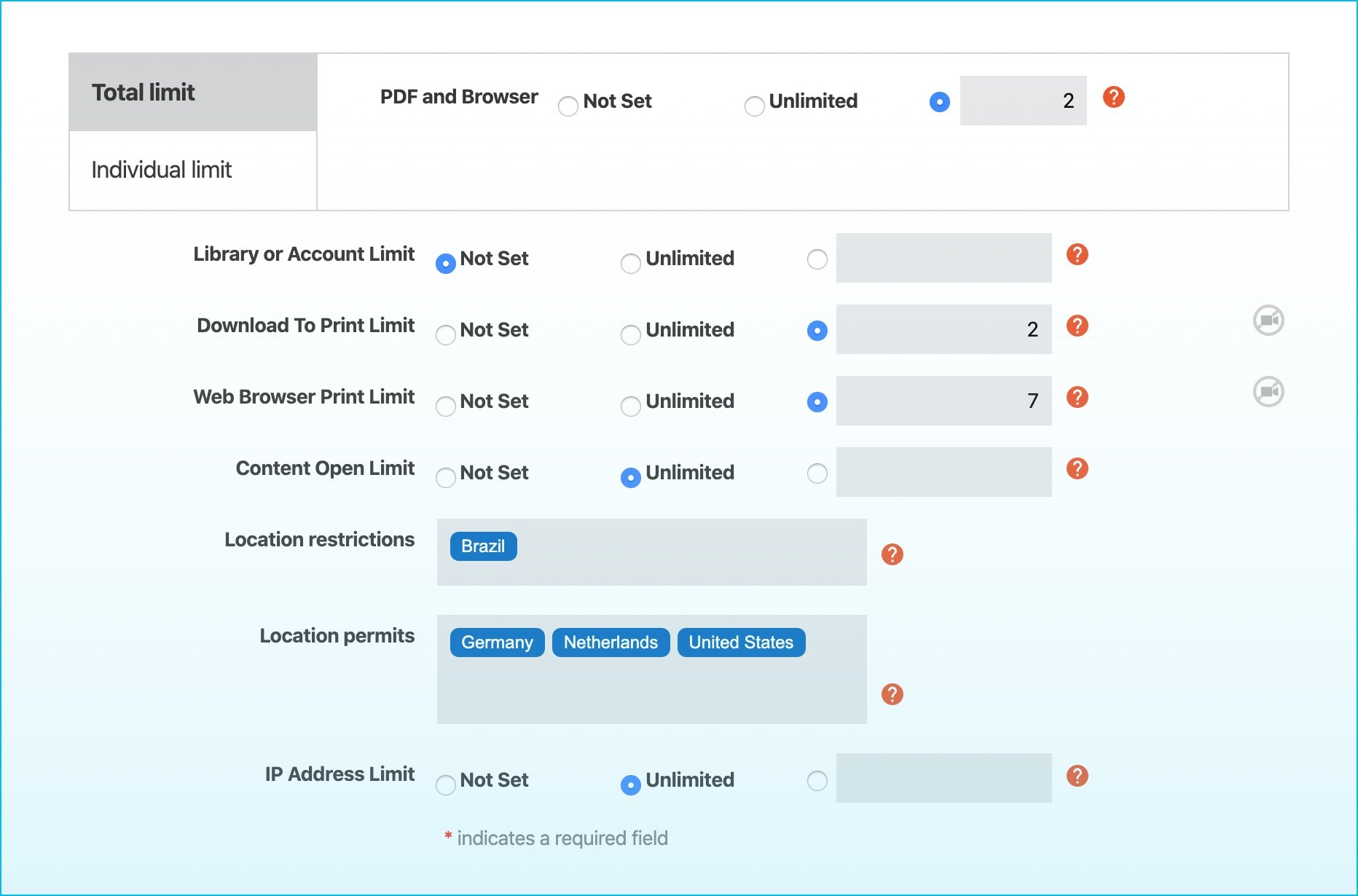
With advanced content protection and DRM solution, every digital asset within your secure data room has the highest level of encryption and access controls. Just a few of the controls you can implement on your digital assets when you use Vitrium Security include:
- Setting authentication measures on individual files
- Blocking printing and copying
- Setting device limits
- Restricting access to certain IP addresses
- Applying content open limits
- Expiring content
- Restricting certain countries
- And more...
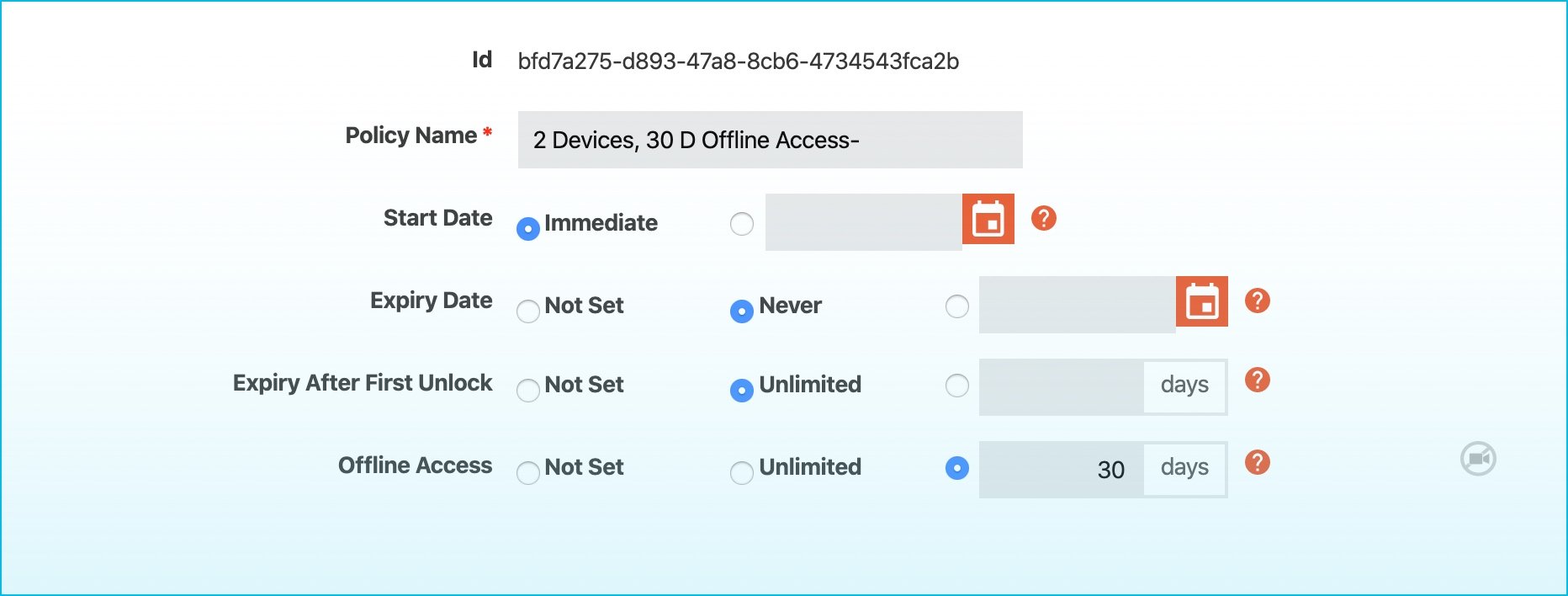
A Quality DRM Solution Provides User Tracking As Well
Imagine being able to see what files authorized users are looking at, what date and time they’re accessing them, whether they’re attempting to download or print them, and even how much time they are spending while accessing files.
The more aware you are of how your digital assets are being used, accessed, and interacted with, the more insights you have about how important or critical your content is. And if you see numerous errors cropping up in the logs, this could be a sign of authorized users attempting to share your files when they're not supposed to, print files when they're not supposed to, or access files outside of their IP address range, all signs of something being amiss.
![]()
Another example would be audio or video files that normally only incur a handful of views suddenly experiencing a significant surge in views. Your analytics report would signal to you that it’s time to investigate what caused the increase.
Perhaps your company sells memberships to view these audio and video files, and a renewal period just occurred. That could explain the surge in views because members who have just paid for access are more likely to open them.
Maybe upon closer inspection of the user tracking log, you discovered that your DRM policy of unlimited devices for your client with 10 employees was fine but you used the same policy for your other client with 10,000 employees. This explains the surge!
Having detailed user tracking like this allows you to make sound business decisions. In this case, you could go back and modify the DRM policy you have in place for that particular client.
The sooner you are made aware of a possible security breach the better. As CSO Online reported, “Speedy responses could be a massive cost saver. Companies [that were] able to detect and contain a breach in under 200 days spent on average $1.2 million less.”
With Vitrium Security, you receive real-time analytical reports that allow you to track all user activity. This instant access could be the difference between a significant breach that costs vital time and resources, and one that comes to a quick resolution. When you have the ability to analyze user behavior such as read-through-rate, time spent on the page, pages viewed, etc… outliers become apparent almost instantly.
You owe it to your clients, employees, shareholders, partners, and more to protect your intellectual property. Learn more about building a secure data room with DRM capabilities.