The Best Protection for Digital Assets:
Virtual Data Rooms with DRM Controls
- Use a Virtual Data Room with File-Level Protection
- DRM Controls Help Organizations Avoid Content Leaks
- Track How Users Are Consuming and Engaging with Content
- Use Case: Education & Training
- Use Case: Financial Firms
- Use Case: Research Companies
- Use Case: Sales and Marketing Teams
- Can Your Industry Benefit from a Virtual Data Room?
- Use a Virtual Data Room with File-Level Protection
- DRM Controls Help Organizations Avoid Content Leaks
- Track How Users Are Consuming and Engaging with Content
- Use Case: Education & Training
- Use Case: Financial Firms
- Use Case: Research Companies
- Use Case: Sales and Marketing Teams
- Can Your Industry Benefit from a Virtual Data Room?
Subscribe to Vitrium Content Security and DRM updates
Use a Virtual Data Room with File-Level Protection
Now more than ever, companies need to think about how they share and distribute their intellectual property.
As more social media platforms and networking websites become more popular in the business world, digital asset protection becomes even more critical. Enter the virtual data room - the best method for securely sharing and distributing confidential or valuable content.
WHAT IS A VIRTUAL DATA ROOM?
In a nutshell, a virtual data room is a secure content portal & distribution platform. When combined with a digital rights management (DRM) solution, a virtual data room transforms what can essentially be an online vault for documents, audio files, video files, and images, to one that controls who can access certain files, for how long, on how many devices, and more.
Though they have been most commonly used by companies for mergers and acquisitions (M&A), virtual data rooms are also useful for any industry that needs to protect their digital assets while storing and distributing content.
VIRTUAL DATA ROOM + DRM CONTROLS
Think of a virtual data room combined with DRM controls analogous to a secure house with the owner's most valuable contents secured in a state-of-the-art safe. The house is safeguarded with locks and an alarm system, much like a virtual data room is protected with password or authentication controls. Then, like the safe in the house, the files within the virtual data room have an extra layer of protection with file-level encryption and digital rights management controls applied to them.

It’s difficult for a would-be criminal to rob a house. However, it is significantly more difficult to access the items inside the safe because of these added security controls. The same is true of your virtual data room. Even if an unauthorized user were to somehow gain access to your secure portal, the file-level protection on each piece of content inside would make your intellectual property that much more difficult to access.
The reason that clients choose Vitrium Security over other companies that offer virtual data room solutions, is that we add much-needed layers of ironclad protection and control to your content. When you set up your virtual data room with us, the content you place inside it is instantly encrypted and secured. Within minutes you can protect your digital assets and share with authorized users, without worrying about unwanted sharing or distribution.
DRM Controls Help Organizations Avoid Content Leaks
There are few scenarios as unnerving for a company as content leaks, and their full impact may not be known until after it occurs.
For some companies, content leaks can result in loss of revenue. For others, the impacts can be far worse, including lawsuits, damage to reputation, and depending on the nature of their business, government fines, and legal action.
Content leaks can include:
- Emails sent to unintended recipients with attachments
- Files downloaded and shared on corporate networks when they shouldn't be
- Confidential video, audio, or document links inadvertently shared on social media websites
- A lost laptop with unprotected files being found
- Authorized users sharing login data
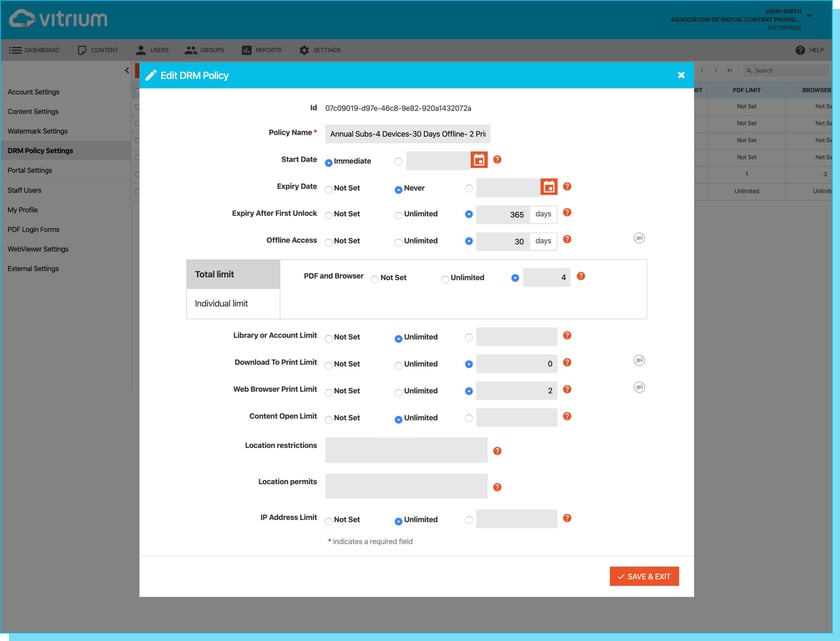
Vitrium's VDR solution allows you to protect your confidential or valuable digital assets, while empowering you to control those assets with different DRM controls:
- Preventing copying or printing
- Setting content expiry dates
- Limiting viewing times
- Restricting certain countries
- Allowing specific IP addresses
Any content that can be easily copied, printed, or shared is prone to many threats like piracy, intellectual property (IP) infringement, mass redistribution, leaks, plagiarism, data breaches, and so on. Particularly vulnerable is content that generates revenue for a business or contains confidential information, trade secrets, financial information, or content that is otherwise sensitive in nature. So in this digital age, what are firms to do?
The first line of defense that comes to mind is to add password-protection on a file. Although passwords can restrict file access, they are often easy to share, easy to crack, and difficult to manage for more than a single user.
Watermarks are also considered and they’re an excellent feature to deter copyright infringement, but not restrictive enough on their own. Adding a dynamic watermark that includes user identifying information such as a user name, user ID, company name, etc. definitely takes things a step further, but again, not restrictive enough on its own.

The best measures are to add strong, military-grade encryption. With this option, you’re essentially converting your unprotected content to a non-readable, encrypted format that can then only be unencrypted when you receive the encryption keys or you’ve been authenticated against another system. The most common encryption level offered by many file sharing and virtual data room providers is disk-level encryption. At this level, only the directory containing the files is encrypted while individual files remain unprotected and still vulnerable to leaks, unauthorized sharing, piracy and other potential hacks.
A great analogy for disk-level encryption is protecting your house with a lock and security system, but leaving all your valuables inside unprotected. A robber could bypass the lock and security system, and then gain access to whatever they find in the house. However, by applying file-level encryption and control in addition to the disk-level encryption is analogous to having a robust digital rights management (DRM) system like Vitrium which protects both the house (or portal / data room where the content resides) and the valuables within the house (the files within the portal or data room). By applying file-level encryption and DRM controls, this secures all the individual files and enforces protection no matter where the content resides.
Track How Users Are Consuming and Engaging with Content
An added benefit of using Vitrium’s data room with DRM controls is that each file can be tracked, providing companies valuable insight into how users are consuming and engaging with their content.
Imagine being able to easily answer questions about your content such as:
- Who are the most active users consuming it?
- Which content is being accessed the most frequently?
- Which file is it?
- Are videos, documents, or audio files more popular?
- How are your users accessing content?
- What country or IP address are they coming from?
- What browser or application are they using?
Having answers to these types of questions can help you develop better content for your users. For example, if you learn your users prefer consuming videos over documents, you may want to create more videos in the future. Or if you find that some content is never accessed, it could be a signal that it’s time to remove it from your product offerings.
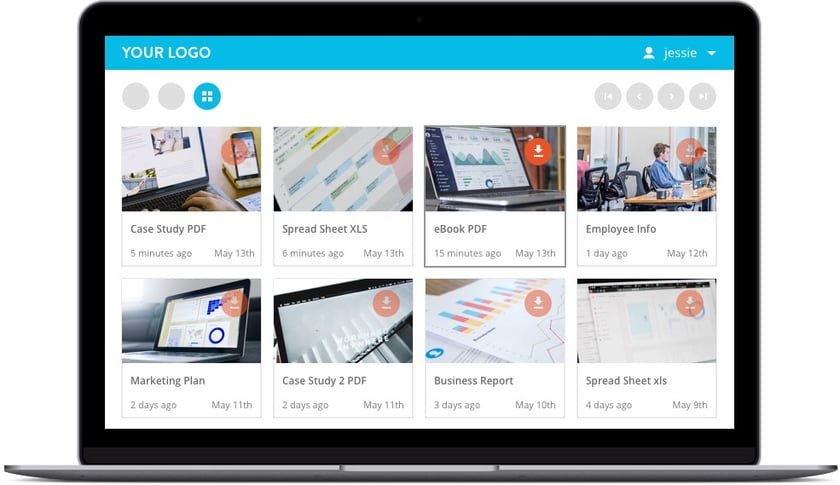
We mentioned earlier that a virtual data room is most frequently associated with the field of mergers and acquisitions (M&A). However, in the age of digital content consumption, a multitude of industries store and distribute content - and that content needs digital asset protection. The next few sections highlight four different examples of companies or teams that can benefit from using a secure data room combined with digital rights management controls.
![]()
Having answers to these types of questions can help you develop better content for your users. For example, if you learn your users prefer consuming videos over documents, you may want to create more videos in the future. Or if you find that some content is never accessed, it could be a signal that it’s time to remove it from your product offerings.
We mentioned earlier that a virtual data room is most frequently associated with the field of mergers and acquisitions (M&A). However, in the age of digital content consumption, a multitude of industries store and distribute content - and that content needs digital asset protection. The next few sections highlight four different examples of companies or teams that can benefit from using a secure data room combined with digital rights management controls.
Use Case: Education & Training
All educational content is valuable and needs to be secured, while also being easily accessible by the right users, those who have been authorized to take the course, paid for the content, or are in the class that the school or school district paid the content for.
Educational content isn’t restricted to only K-12 or college and university students. It can also be delivered by, and to, industry-related associations, eLearning institutions, professional training organizations, or even corporate training departments.

With regards to students or trainees, using a virtual data room allows them to log into one secure portal and have instant access to all of their lessons or study materials. The content provider can upload their documents, videos, and audio files, set the appropriate content and DRM controls, and assign permission to the right groups or individuals.
Add your logo to the portal and customize the colors to match your organization's brand. You can even customize how your folders look! If you're a larger organization or already have a system in place to distribute your content, Vitrium can easily be integrated with your own website or a third-party platform such as a learning management system (LMS).
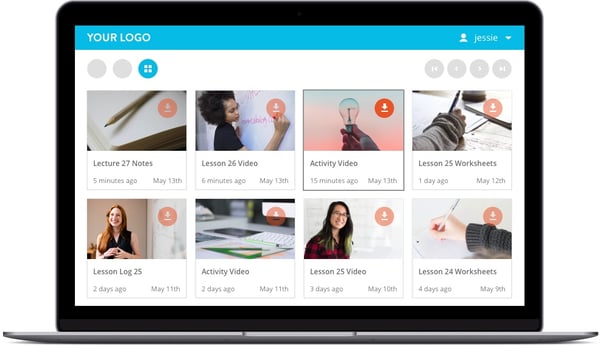
Once your portal is set up, users can be provided with single sign-on (SSO) access to log in and view materials for as long as you want them to have the ability to. For example, if the training period is only 90 days, you could set an expiry date of 90 days for the materials to ensure that users don’t share the materials with the next round of trainees.
You can also prevent printing and copying of the materials so that only the people that are allowed to see them will have access. And you can apply user-identifying watermarks to the content (and take advantage of Vitrium's 'hidden watermark' feature) for that rare case when someone does decide to take screenshots and tries to recreate your content.
Then, using Vitrium’s advanced tracking and analytics, you can view how people are engaging with and consuming your materials. The insights you gain from these analytics will help you improve the quality of your content, discover ways to help users that may be struggling, and ultimately increase the number of people who would like to pay for your content!
Use Case: Financial Firms
Financial firms such as M&A firms, investment or asset management companies, private equity firms, hedge funds, insurance companies, and financial research organizations need virtual data rooms combined with DRM capabilities to protect the confidential and sensitive financial information in their business.
Regardless of your company size, leaks of your information can cost a financial firm time, money, and reputation. It is therefore essential that things like client data, research data, price reports, investment proposals, and even newsletters are not accessible by unauthorized users.
Suppose your company is trying to manage the merger between two organizations. In the event a leak occurs, it could impact the stock price, community opinion, and pending client contracts for purchases and sales. Until a merger is made public, all information related to it must be kept private, otherwise, the deal could fall through. If a leak were to occur, it might destroy the deal costing both companies untold amounts of revenue and undue stress.
Another example would be a financial research company that provides a highly sought-after weekly price report for the commodities market. Their critical information can help firms determine when to buy, sell, or where to invest money. However, if the information they are selling were to leak, it could alter the current market conditions resulting in fewer profits for everyone. Bottom line - if you are working in a financial firm, subscribing to a virtual data room solution that combines the power of DRM control and analytics is an absolute must!

Use Case: Research Companies
Research Companies rely on secure portals not just to protect their IP, but also to protect their revenue and their reputation. The simple fact is that if content can be accessed freely, users are much less likely to pay for it in the future. After all, why pay for something that is easy to access through a third party?
Imagine for a moment that you’re on a research team that has been analyzing the Google search algorithm, and you have identified relatively unknown or unused ways that marketing teams can better utilize keywords to organically rank higher in search engine results pages (SERPs).

Now suppose your clients pay your company for access to research publications to get the upper hand on their competitors using your recommendations. If one of your customers were to excitedly share the publication with a friend, that might not have an immediate negative impact. That is until that friend shares it on LinkedIn and suddenly your publication is going viral rendering your organic search strategies useless.
If instead, your organization used a secure virtual data room to distribute their research reports, one with strong DRM controls on each file that prevented sharing with unauthorized clients, your content would have been locked up, and your paying users could have enjoyed the full benefits of using your research, and you could have earned more revenue had that same person shared the link to the report for others to buy!

Use Case: Sales and Marketing Teams
Sales and marketing teams that wish to distribute confidential information such as their price lists, partner lists, sensitive new product information, original design specs, trade secrets or more, need a virtual data room with DRM controls to have peace of mind knowing their valuable digital assets are protected and controlled at all times.
They can also check up on who's viewing or accessing their content at any time with the added benefit of tracking capabilities.
![]()
If you think this information doesn’t need ironclad protection, consider this scenario:
Imagine the fictitious company Y2B Computers has been developing design specifications on a new laptop that has a longer battery life and is lighter in weight than the competition’s laptop. Y2B isn’t quite ready to bring this project to the prototype stage, but they are discussing possibilities with production companies to see how they could go about mass producing the laptop to sell it at a lower price point than their competitors. Just one problem - they aren’t using a virtual data room to share the specs with the production companies.
One of the companies is so impressed with the design specs, they decide to cut out the middleman and try to produce the laptop without Y2B. They download the files, and within months a knockoff of the original design hits the shelves and at a fraction of the cost that Y2B was going to sell it for. This could have been avoided with a virtual data room and file-level DRM controls.

Your sales and marketing teams need to share information with authorized users, and it needs to be easily accessible by those people. However, it’s critical that your content can’t be swiped, copied, or duplicated. At the very least, unauthorized access to your valuable IP could cost you untold amounts of revenue.
Can Your Industry Benefit from a Virtual Data Room?
If you are creating and distributing valuable or sensitive content, the answer is yes!
We’ve only covered a handful of examples that express how beneficial a virtual data room with DRM controls is, barely scratching the surface of what Vitrium Security can do for your organization!
Since 2005 Vitrium has been securing content, and with more than one million users worldwide accessing content that we protect, we are one of the most widely deployed solutions for content security on the market.
Learn more about how Vitrium can help you protect your content

Curious which DRM solution is best for your business?
CONTACT US
© Copyright 2026 Vitrium Systems Inc.
