FAQ Category: Content Distribution
Get your questions answered from our list of frequently asked questions.
- What are the different ways to distribute Vitrium-protected content?
-
There are numerous ways you can distribute your Vitrium-protected content and it will largely depend on which Vitrium application you have:
Vitrium Security Pro Vitrium Security Enterprise VitriumOne Send protected content via:
- Custom user portal
- Email with hyperlinks
- Website with hyperlinks
Send protected content via:
- Another business system such as an LMS, CRM, AMS, eCommerce, etc.
- Custom user portal
- Email with hyperlinks
- Website with hyperlinks
Send protected content via:
- VitriumOne customized portal
- eCommerce system
- How do I know if a User is accessing content on multiple devices?
-
If you want to check out a user’s activity you need to review “User Activity Log” report in Reports tab. You can access a specific user’s activity report whether by filtering the report by the User Name or going to the Users tab and click on the report icon
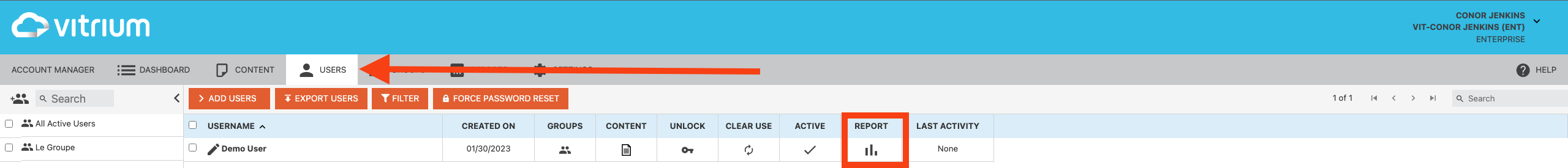
This report shows the date and time when a file was accessed, what the file name is, which user accessed the file, which group the user belongs to, which method they used to unlock the file (web or PDF), which IP address they used to unlock from, what their tracking ID is (a specific ID from their application or browser’s cookie), and also which application or browser was used, what version, and what operating system they used.
If there are different Tracking IDs or different IP addresses, it means that the user has unlocked or tried to unlock the content from different devices and from different locations. Note that Secured PDF files can only be accessed in Adobe Reader or Acrobat on a desktop or Laptop so the Application shown for secured PDF content is only Reader; However, Secured web links are accessible through a browser whether in desktops, smartphones or tablets.
- How can I add/view the Table of Contents in the web viewer?
-
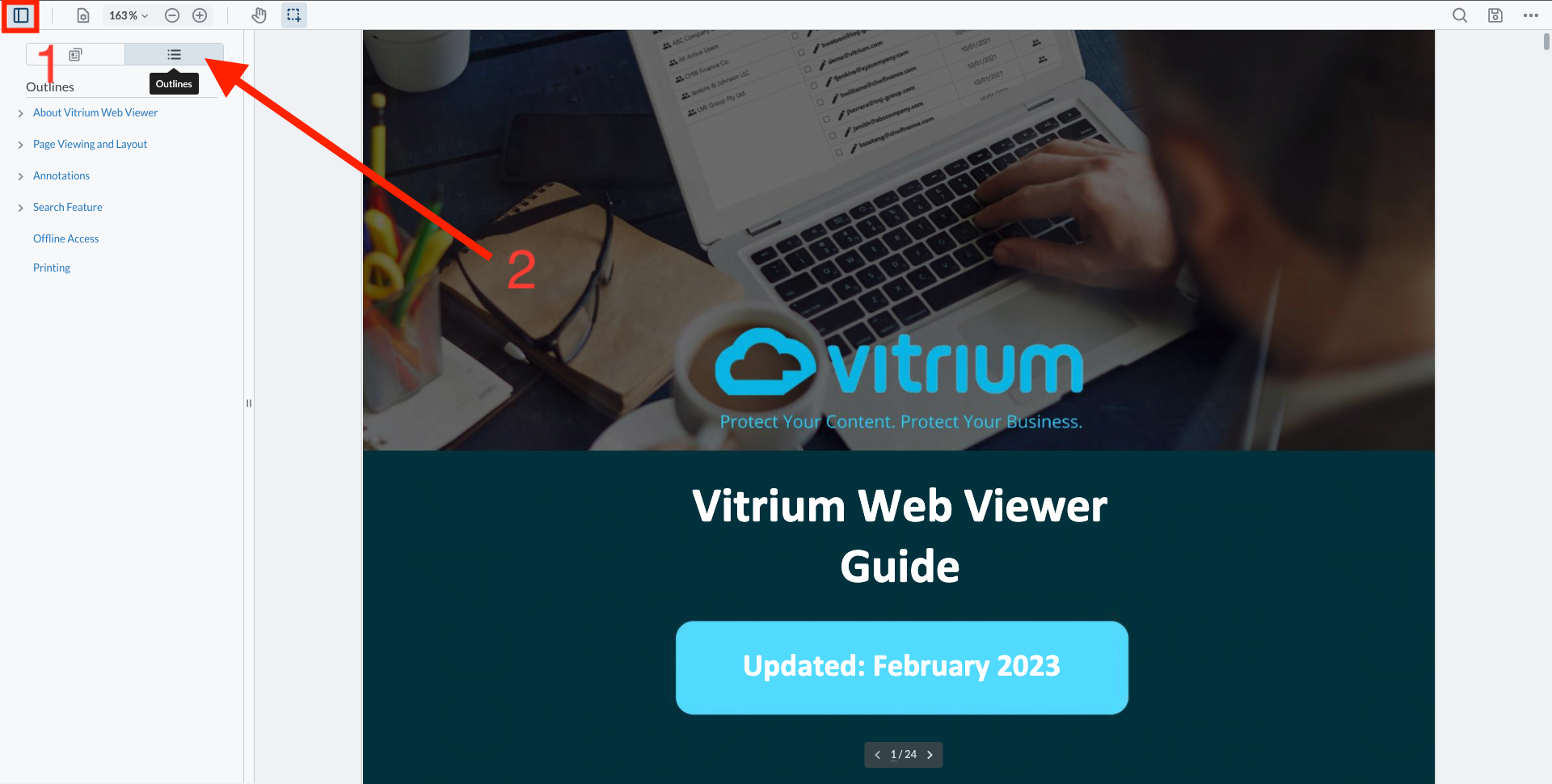
To view the Outlines or Table of Contents in the Vitrium Web Viewer, click the ‘Panel’ button on the left-hand side of the web viewer, then click the Outlines icon.
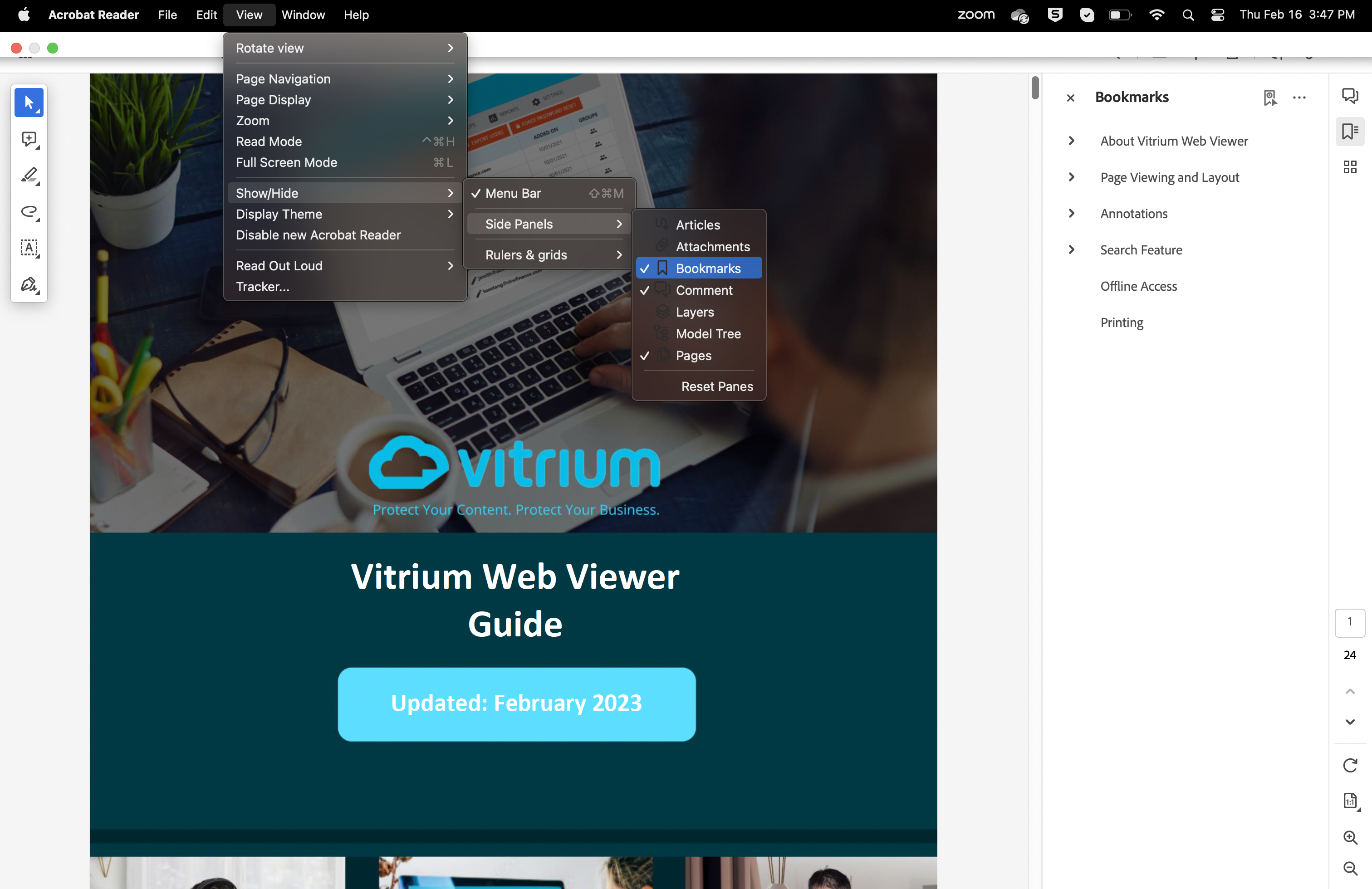
To view the Bookmarks in Adobe Reader, click the ‘View’ button, then click Show/Hide > Side Panels and check the Bookmarks option.
- What is the difference between offline days and expiry date?
-
Offline days, when greater than 0, allows Web Viewer users to click the toolbar icon "Save to Browser" and save that content to the browser's cache and be offline -- no Internet access -- for those number of days. The user would also have to bookmark the Web Viewer URL in order to access that content offline. Once the number of days lapses, if the user is online, they will automatically be authenticated once again and be granted another (N) days offline. If the user is offline, the content will be locked and the user logged out. The user will need to be online and log in once again to continue to access the content. This re-authentication forces the Webviewer content to communicate back with Vitrium’s server to re-validate the User’s authenticity while checking if the content and/or DRM policy is still valid.
Expiry date is when content is set to expire, depending on the level the DRM Policy is set, it renders all access for the User(s) or Group(s) to be denied when the date comes. This is determined by setting a specific date of expiry.
Thus, the most predominant difference is that Offline days used for those users who can’t connect to the internet and this feature enables them to have access to the protected content without an internet connection. On the other hand, Expiry dates limits user(s) or group(s) from accessing the content after the date you’ve set. Subscription-based businesses can benefit from the Expiry date feature and also expiry after first unlock.
NOTE: If Expiry date is set, offline days will be shortened if it allows the user to go beyond the expiry date.
- Where can I find information on Vitrium's API Guides and sample code?
-
Please refer to our Knowledge Base article here: https://www.vitrium.com/knowledgebase/guides/vitrium-security-api-guides/